Hi Everyone, recently I’ve discovered vulnerability in SeedDMS engine which could let attacker to takeover any account (Including Administrator).
Without further wasting your time let’s dive into the details.
- CWE-640: Weak Password Recovery Mechanism for Forgotten Password
- CWE-770: Allocation of Resources Without Limits or Throttling
Application allows user to reset password by visiting the URL sent on the email, on a surface, it look quiet normal but once we dive into source code, the things are totally different.
Overview of vulnerability
in order to reset password for the user SeedDMS generates md5 hash, the SeedDMS by itself is written in PHP, and SeedDMS generates md5 of the result of uniqid() function, which takes two parameters: string $prefix = “”, bool $more_entropy = false) and returns string, SeedDMS passes time() function as first argument which returns unix time stamp, and it’s being used as a prefix, but uniqid by itself also uses unix time stamp to generate the “Unique ID”, which makes result of the function predictable, if you know when it was being called.
and when I discovered this vulnerability, it existed in every version of SeedDMS ever released.
Proof of concept
Prerequisite:
you need to know username and email of the victim account to request password reset, by default for administrator SeedDMS uses admin and [email protected].
if you have low privilege access on the system, you can find other users via search feature, which disclosures their email and username.
Source of vulnerability:
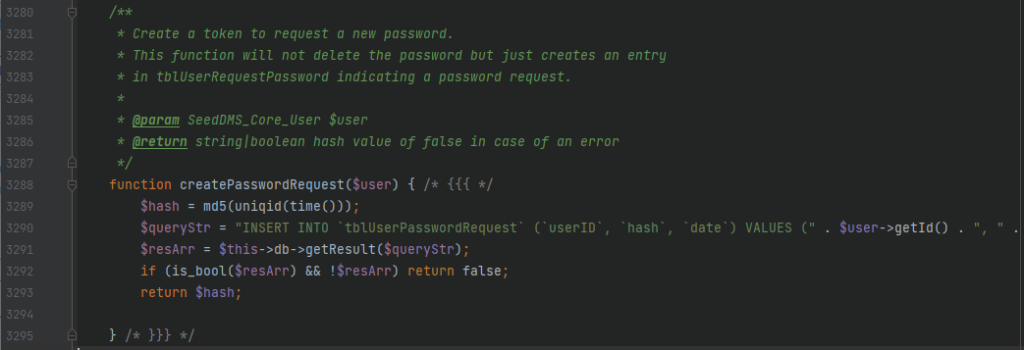
vulnerability exists in /pear/SeedDMS/Core/inc.ClassDMS.php file, which holds most of the core functionality of SeedDMS
As you can see, on line 3289 the $hash variable is being generated, which is md5 of uniqid(time()) if we take a look at uniqid functions source code of PHP here.
you’ll see that uniqid by itself also uses unix time and gets hex values of unix time stamp, to be specific, first 8 hex chars of uniqid is Unixtime and 5 hex chars are microseconds
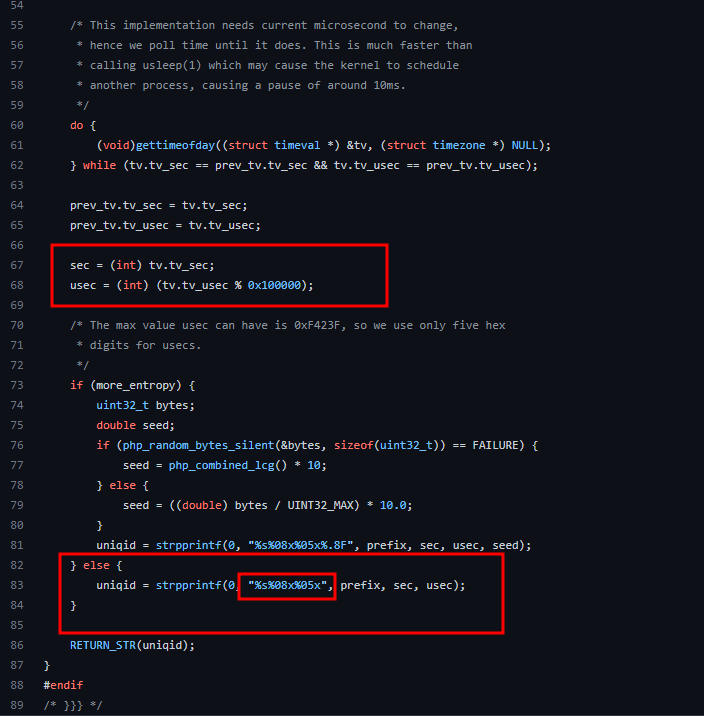
and $prefix is just a prefix appended on result of operations on unix time
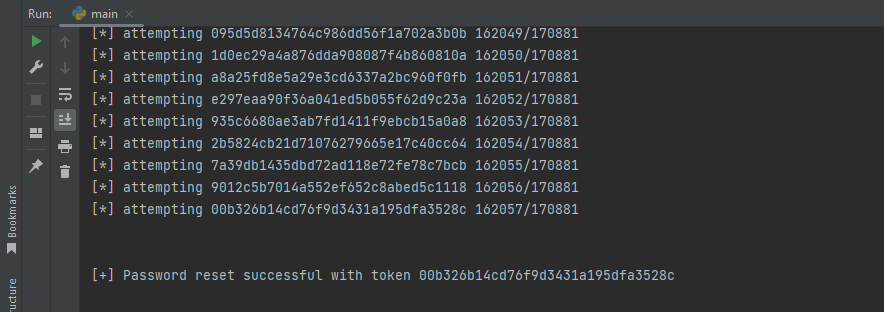
If you’ll generate potential hashes list based on request send time and response receive (including 0.15 second delta – since we’re dealing with microseconds there might be a difference), you’ll end up with nearly 180,000 potential hashes, and What is important is that there’s no any kind of limit on reset attempts.
all you have to do is just fire them all on password reset request, and upon successful guess, password will be changed and you’ll take over the account.
I’ve written small exploit code which takes like 20 min with single thread and 3-4 min with FFUF tool (100 thread) to brute force valid hash
Patch / Solution:
I’ve reported vulnerability to SeedDMS after I discovered it and I got response next evening from Uwe Steinmann.
within two weeks from reporting he released updates for both branches including fix for this vulnerability.
So best solution is to get SeedDMS 5.1.28 or newer (Version 5 Branch) or SeedDMS 6.0.21 or newer (Version 6 Branch) from official sources:
- https://www.seeddms.org/
- https://sourceforge.net/projects/seeddms/
CVE Status:
- CVE Published with ID: CVE-2022-44938
