PowerView is a PowerShell tool to gain network situational awareness on Windows domains. It contains a set of pure-PowerShell replacements for various windows “net *” commands, which utilize PowerShell AD hooks and underlying Win32 API functions to perform useful Windows domain functionality.
In this post, I’ll write down few PowerView Commands which might be useful in AD Enumeration.
You can download PowerView from here: https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
Importing PowerView
Import-Module .\PowerView.ps1Get-NetDomain
Get current users domain info
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetDomain
Forest : ducks.local
DomainControllers : {DC01.ducks.local}
Children : {}
DomainMode : Unknown
DomainModeLevel : 7
Parent :
PdcRoleOwner : DC01.ducks.local
RidRoleOwner : DC01.ducks.local
InfrastructureRoleOwner : DC01.ducks.local
Name : ducks.local
Get-NetForest
Get current users domains forest info
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetForest
RootDomainSid : S-1-5-21-3676834494-100404595-163698713
Name : ducks.local
Sites : {Default-First-Site-Name}
Domains : {ducks.local}
GlobalCatalogs : {DC01.ducks.local}
ApplicationPartitions : {DC=ForestDnsZones,DC=ducks,DC=local, DC=DomainDnsZones,DC=ducks,DC=local}
ForestModeLevel : 7
ForestMode : Unknown
RootDomain : ducks.local
Schema : CN=Schema,CN=Configuration,DC=ducks,DC=local
SchemaRoleOwner : DC01.ducks.local
NamingRoleOwner : DC01.ducks.localGet-NetDomainController
Returns DC for current or specified domain
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetDomainController
Forest : ducks.local
CurrentTime : 4/13/2022 7:44:25 AM
HighestCommittedUsn : 20730
OSVersion : Windows Server 2019 Standard Evaluation
Roles : {SchemaRole, NamingRole, PdcRole, RidRole...}
Domain : ducks.local
IPAddress : 192.168.232.132
SiteName : Default-First-Site-Name
SyncFromAllServersCallback :
InboundConnections : {}
OutboundConnections : {}
Name : DC01.ducks.local
Partitions : {DC=ducks,DC=local, CN=Configuration,DC=ducks,DC=local,
CN=Schema,CN=Configuration,DC=ducks,DC=local, DC=DomainDnsZones,DC=ducks,DC=local...}
Get-DomainPolicy
Gets information about domain policy
PS C:\Users\ssmith.DUCKS\Desktop> Get-DomainPolicy
RegistryValues : @{MACHINE\System\CurrentControlSet\Control\Lsa\NoLMHash=System.String[]}
SystemAccess : @{MinimumPasswordAge=1; MaximumPasswordAge=42; LockoutBadCount=0; PasswordComplexity=1;
RequireLogonToChangePassword=0; LSAAnonymousNameLookup=0; ForceLogoffWhenHourExpire=0;
PasswordHistorySize=24; ClearTextPassword=0; MinimumPasswordLength=7}
Version : @{Revision=1; signature="$CHICAGO$"}
KerberosPolicy : @{MaxTicketAge=10; MaxServiceAge=600; MaxClockSkew=5; MaxRenewAge=7; TicketValidateClient=1}
Unicode : @{Unicode=yes}
Get-NetUser
Gets information about specific (if username specified) or all users
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetUser ssmith
logoncount : 8
badpasswordtime : 4/12/2022 11:51:07 PM
description : Sam is good guy, he's using password Passw0rd
distinguishedname : CN=sam smith,CN=Users,DC=ducks,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : sam smith
lastlogontimestamp : 4/12/2022 11:44:09 PM
userprincipalname : [email protected]
name : sam smith
objectsid : S-1-5-21-3676834494-100404595-163698713-1105
samaccountname : ssmith
lastlogon : 4/13/2022 12:11:56 AM
codepage : 0
samaccounttype : 805306368
whenchanged : 4/13/2022 7:58:45 AM
accountexpires : 9223372036854775807
countrycode : 0
adspath : LDAP://CN=sam smith,CN=Users,DC=ducks,DC=local
instancetype : 4
objectguid : dbfa1d6c-20e2-4a9f-8ecd-c00ddbb6aae5
sn : smith
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=ducks,DC=local
dscorepropagationdata : 1/1/1601 12:00:00 AM
givenname : sam
memberof : CN=LocalAdmins,OU=Groups,DC=ducks,DC=local
whencreated : 4/13/2022 6:27:07 AM
badpwdcount : 0
cn : sam smith
useraccountcontrol : 4260352
usncreated : 20644
primarygroupid : 513
pwdlastset : 4/12/2022 11:27:07 PM
msds-supportedencryptiontypes : 0
usnchanged : 20736
Get-NetUser -SPN
Get Kerberoastable Users
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetUser -SPN
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
description : Key Distribution Center Service Account
distinguishedname : CN=krbtgt,CN=Users,DC=ducks,DC=local
objectclass : {top, person, organizationalPerson, user}
name : krbtgt
primarygroupid : 513
objectsid : S-1-5-21-3676834494-100404595-163698713-502
whenchanged : 4/12/2022 7:53:50 AM
admincount : 1
codepage : 0
samaccounttype : 805306368
showinadvancedviewonly : True
accountexpires : 9223372036854775807
cn : krbtgt
adspath : LDAP://CN=krbtgt,CN=Users,DC=ducks,DC=local
instancetype : 4
objectguid : 1dbd9958-8bee-465e-adfa-7b618859d46c
lastlogon : 12/31/1600 4:00:00 PM
lastlogoff : 12/31/1600 4:00:00 PM
samaccountname : krbtgt
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=ducks,DC=local
dscorepropagationdata : {4/12/2022 7:53:50 AM, 4/11/2022 9:04:43 PM, 1/1/1601 12:04:16 AM}
serviceprincipalname : kadmin/changepw
memberof : CN=Denied RODC Password Replication Group,OU=Groups,DC=ducks,DC=local
whencreated : 4/11/2022 9:04:42 PM
iscriticalsystemobject : True
badpwdcount : 0
useraccountcontrol : 514
usncreated : 12324
countrycode : 0
pwdlastset : 4/11/2022 2:04:42 PM
msds-supportedencryptiontypes : 0
usnchanged : 16572
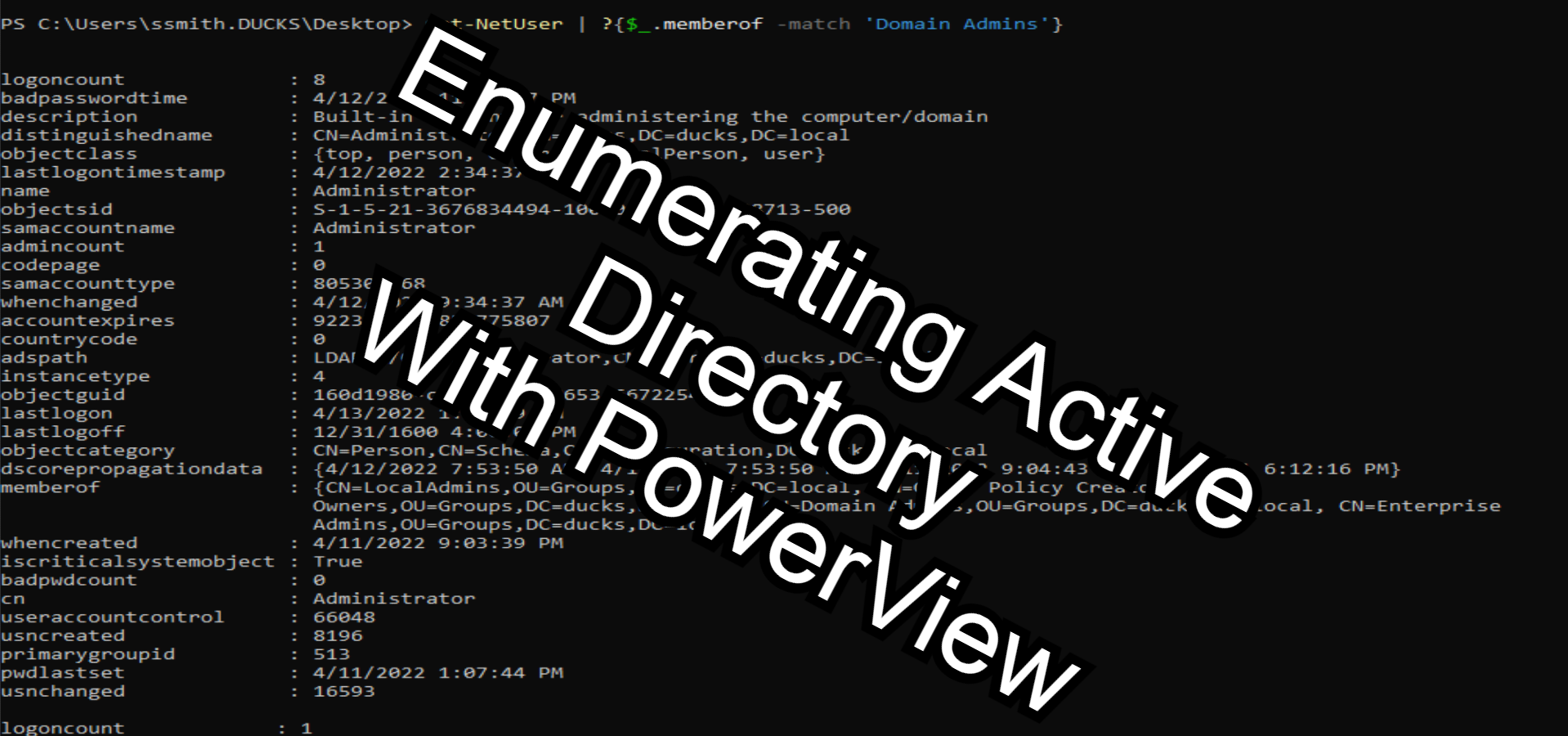
Get-NetUser | ?{$_.memberof -match ‘Domain Admins’}
Get Domain Admins
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetUser | ?{$_.memberof -match 'Domain Admins'}
logoncount : 8
badpasswordtime : 4/12/2022 11:42:47 PM
description : Built-in account for administering the computer/domain
distinguishedname : CN=Administrator,CN=Users,DC=ducks,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 4/12/2022 2:34:37 AM
name : Administrator
objectsid : S-1-5-21-3676834494-100404595-163698713-500
samaccountname : Administrator
admincount : 1
codepage : 0
samaccounttype : 805306368
whenchanged : 4/12/2022 9:34:37 AM
accountexpires : 9223372036854775807
countrycode : 0
adspath : LDAP://CN=Administrator,CN=Users,DC=ducks,DC=local
instancetype : 4
objectguid : 160d1980-c451-4e91-8653-6672254f7ad1
lastlogon : 4/13/2022 1:13:59 AM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=ducks,DC=local
dscorepropagationdata : {4/12/2022 7:53:50 AM, 4/12/2022 7:53:50 AM, 4/11/2022 9:04:43 PM, 1/1/1601 6:12:16 PM}
memberof : {CN=LocalAdmins,OU=Groups,DC=ducks,DC=local, CN=Group Policy Creator
Owners,OU=Groups,DC=ducks,DC=local, CN=Domain Admins,OU=Groups,DC=ducks,DC=local, CN=Enterprise
Admins,OU=Groups,DC=ducks,DC=local...}
whencreated : 4/11/2022 9:03:39 PM
iscriticalsystemobject : True
badpwdcount : 0
cn : Administrator
useraccountcontrol : 66048
usncreated : 8196
primarygroupid : 513
pwdlastset : 4/11/2022 1:07:44 PM
usnchanged : 16593
logoncount : 1
badpasswordtime : 4/13/2022 12:24:50 AM
distinguishedname : CN=Bob Smith,CN=Users,DC=ducks,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : Bob Smith
lastlogontimestamp : 4/13/2022 12:09:22 AM
userprincipalname : [email protected]
name : Bob Smith
lockouttime : 0
objectsid : S-1-5-21-3676834494-100404595-163698713-1103
samaccountname : bsmith
admincount : 1
codepage : 0
samaccounttype : 805306368
whenchanged : 4/13/2022 7:09:22 AM
accountexpires : 9223372036854775807
countrycode : 0
adspath : LDAP://CN=Bob Smith,CN=Users,DC=ducks,DC=local
instancetype : 4
usncreated : 20616
objectguid : 6fa05c92-a40d-4597-99d2-021b0b708e8d
sn : Smith
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=ducks,DC=local
dscorepropagationdata : {4/13/2022 6:35:44 AM, 1/1/1601 12:00:00 AM}
givenname : Bob
memberof : {CN=Domain Admins,OU=Groups,DC=ducks,DC=local, CN=Remote Desktop
Users,CN=Builtin,DC=ducks,DC=local, CN=Administrators,CN=Builtin,DC=ducks,DC=local}
lastlogon : 4/13/2022 12:09:22 AM
badpwdcount : 1
cn : Bob Smith
useraccountcontrol : 66048
whencreated : 4/13/2022 6:24:54 AM
primarygroupid : 513
pwdlastset : 4/12/2022 11:24:54 PM
usnchanged : 20721
Get-DomainPolicy
Gets information about domain policy
PS C:\Users\ssmith.DUCKS\Desktop> Get-DomainPolicy
RegistryValues : @{MACHINE\System\CurrentControlSet\Control\Lsa\NoLMHash=System.String[]}
SystemAccess : @{MinimumPasswordAge=1; MaximumPasswordAge=42; LockoutBadCount=0; PasswordComplexity=1;
RequireLogonToChangePassword=0; LSAAnonymousNameLookup=0; ForceLogoffWhenHourExpire=0;
PasswordHistorySize=24; ClearTextPassword=0; MinimumPasswordLength=7}
Version : @{Revision=1; signature="$CHICAGO$"}
KerberosPolicy : @{MaxTicketAge=10; MaxServiceAge=600; MaxClockSkew=5; MaxRenewAge=7; TicketValidateClient=1}
Unicode : @{Unicode=yes}
Get-NetComputer
Gets list of computers inside domain
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetComputer
DC01.ducks.local
client01.ducks.local
Get-NetOU
returns information about organization units
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetOU
LDAP://OU=Domain Controllers,DC=ducks,DC=local
LDAP://OU=Groups,DC=ducks,DC=local
LDAP://OU=Workstations,DC=ducks,DC=local
LDAP://OU=Backups,DC=ducks,DC=local
Get-NetGroup
Get Groups List
PS C:\Users\ssmith.DUCKS\Desktop> Get-NetGroup | Select-String "Admin"
Administrators
Hyper-V Administrators
Storage Replica Administrators
Schema Admins
Enterprise Admins
Domain Admins
Key Admins
Enterprise Key Admins
DnsAdmins
LocalAdmins
Note: Select String is powershell function which can be used to filter results
Invoke-Userhunter
Find machines where users are logged in
PS C:\Users\ssmith.DUCKS\Desktop> Invoke-UserHunter
UserDomain : DUCKS
UserName : bsmith
ComputerName : client01.ducks.local
IP : 192.168.232.133
SessionFrom :
LocalAdmin :
UserDomain : DUCKS
UserName : bsmith
ComputerName : client01.ducks.local
IP : 192.168.232.133
SessionFrom :
LocalAdmin :
UserDomain : DUCKS
UserName : bsmith
ComputerName : client01.ducks.local
IP : 192.168.232.133
SessionFrom :
LocalAdmin :
Note: this command queries all machines which might be suspicious
That's all for now, Happy Hacking.