Finding Vulnerabilities in Victure RX1800 Wi-Fi Router

Hello Everyone, It’s been a while Since I’ve wrote anything, It’s been a busy period and lots of stuff to deal with, And today, I’d like to share with you my First Attempt of hardware hacking!

Hello Everyone, It’s been a while Since I’ve wrote anything, It’s been a busy period and lots of stuff to deal with, And today, I’d like to share with you my First Attempt of hardware hacking!
Hi Everyone, It’s been a while since I’ve posted something, due to lots of stuff to deal with, lack of motivation and etc. but today we’ll be doing Flick II from OSWE Like Machines List.

Hi everyone, today we’re doing Raven 2 from Vulnhub, and after previous post, I decided to write 0Click RCE exploits for every OSWE Like machine, so this one will be no different. you can get this machine from here

Hi Everyone, today we’re doing Machine from vulnhub called “Secure Code”, which I picked from OSWE Like Machines list.

Hi Everyone, It’s been a while since I posted something, and today, we’re doing Ted from Vulnhub in where we’ll dive into PHP web app with complex file inclusion vulnerability

Hi Everyone, recently I’ve discovered vulnerability in SeedDMS engine which could let attacker to takeover any account (Including Administrator). Without further wasting your time let’s dive into the details.

Hey, today we’re doing Blocky from hack the box, Which is quiet easy and interesting machine If you’ve seen “OSWE Like Machines” list, this one is in it, so if you are on your way to get OSWE, this might…

Today we’re doing a machine from VulnHub called: “The Planets: Earth”; this machine’s difficulty level is easy. In this machine we’ll have to play with XOR and do little bit of reversing.

Once you gain access to the host, it’s important to always be able to repeat that, but sometimes it’s hard to re-exploit a vulnerability that you just did because of its complexity or any other reason. sometimes you need specific…
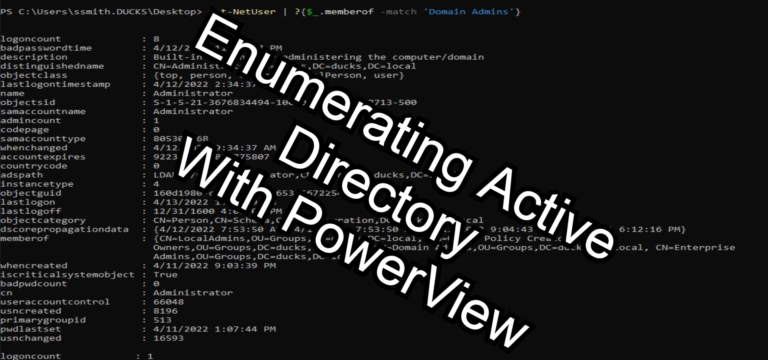
PowerView is a PowerShell tool to gain network situational awareness on Windows domains. It contains a set of pure-PowerShell replacements for various windows “net *” commands, which utilize PowerShell AD hooks and underlying Win32 API functions to perform useful Windows…